Industrial Internet of Things

Our research can be categorized into the following four areas:
- Secure Industrial Collaboration
- Network Security
- Device Security
- In-Network Processing
Secure Industrial Collaboration
We look into security & privacy aspects of interorganizational dataflows. In particular, we consider two main research directions.
- Collaboration along existing supply chains with the intention to …
- reduce costs and improve the productivity
- improve the product quality, provide more accurate lifetime estimates, and more
- dynamically react to change requests
- Collaboration across supply chains with the benefits of …
- unlocking knowledge (e.g., ideal machine configurations, material behavior, …) available at companies in a related (or identical) domain
- reducing the overhead of adjusting existing and setting up new production lines
- comparing performance and productivity
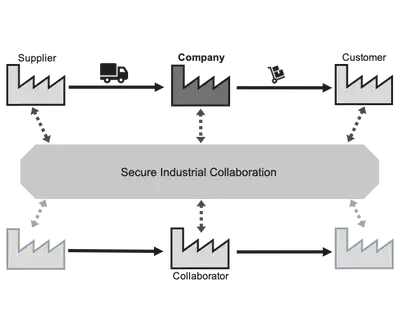
Depending on the sensitivity of (exchanged) information and the level of established trust between the individual use case requirements differ significantly. Identifying new suitable collaborators (not limited to suppliers) is a challenging task as no central register indexing all knowledge and offered services exists, and both involved parties have no established trust relationship.
More details on our work in the area of secure industrial collaboration.
Network Security
Industrial collaborations and reduction of costs, e.g., by centralizing the control of several production lines, goes hand in hand with the interconnection of formerly isolated industrial networks to the Internet. As this introduces a variety of attack vectors, operators need mechanisms to secure their systems. However, not all solutions known from IT networks are directly applicable to industrial networks. Therefore, we research in two main directions regarding network security:
- Intrusion detection enabling operators to
- detect and analyze malicious external connection attempts.
- recognize changes in device behavior, e.g., when devices are compromized.
- evaluate the behavior of brought devices connected to the internal network, e.g., as allowed by the BYOD policy.
- Secure-by-default communication mechanisms
- enabling legacy industrial devices to communicate securely.
- reducing the risk of misconfigured deployments.
- minimizing the attack surface to prevent undesired access to devices from the outset.
Contact: For questions and inquiries regarding Industrial Network Security please contact Ina Fink or Markus Dahlmanns.
Device Security
As security requirements not only must be addressed by the network configuration but also affects the devices connected to the network, in our research we also take device security into account. Basically, we analyze the following aspects of deployed industrial devices.
- Openly accessible device information, e.g., device type and software version.
- Security configuration when security is a built in feature.
Contact: For questions and inquiries regarding Industrial Device Security please contact Markus Dahlmanns.
In-Network Processing
Industrial automation and control systems are characterized by diverse requirements, ranging from latency-critical processes, e.g., remote-controlled robots, to bandwidth-intensive use cases where large amounts of sensor data have to be transmitted, e.g., for documentation purposes. The wide range of requirements, which sometimes even contradict, challenges traditional IP-based networks as they are designed for unreliable best-effort traffic. Realizing new concepts such as Industry 4.0 or the Internet of Production thus requires adapting the existing networking technologies and developing new mechanisms.
In-Network Processing (INP) offers one way of making the networks ready for the envisioned use cases. The main idea of INP is to deploy computational functionality directly on networking hardware, e.g., switches or routers, to process data as early as possible which has benefits for several scenarios:
- Low-latency applications: Simplified control functionality can be placed into the network which can process sensor information and return rough control information to actuators.
- High bandwidth needs: The network load can be reduced by filtering out unimportant data or by performing preprocessing steps as soon as possible. One example is the iterative calculation of minimal reported sensor values.
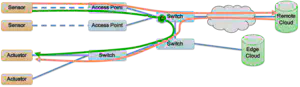
Strategically placing INP functionality can thus improve the overall system performance while also allowing for diverse applications. Overall, our research especially focuses around the following topics:
- Identifying and analyzing concrete problems in industrial networks
- Devising adapted INP functionality to solve the analyzed issues
- Solving general transport-related issues inherent to INP as a whole
With our research, we contribute to the IRTF Computing in the Network Research Group.
Contact: For questions and inquiries regarding In-Network Processing please contact Ike Kunze or René Glebke.
Teaching
We offered the following teaching activities specifically concerning the Industrial Internet of Things.
Research Focus Classes on …
- Cyber-Physical System Security (WS 19/20)
- In-Network Processing (WS 19/20)
- Securing Industrial Networks (SS 21)